Security management
At Cloudera, safeguarding your data is our top priority. We use industry-leading measures and comprehensive protocols to provide a secure environment to protect your data.
Internal audit
Cloudera conducts internal audits to continuously monitor our environment, detect discrepancies, and ensure policy standards.
Penetration testing
Cloudera conducts internal and third-party penetration tests to simulate attacks, expose vulnerabilities, and enhance security. Request our latest pentest results here.
Business continuity
Our Business Continuity policy details processes and planning for handling catastrophic events, ensuring prompt response and high availability of our products for customers.
Incident response
Cloudera proactively defends against threats with effective incident response, detecting suspicious activity and security incidents. Learn more about our Incident Management process here.
Risk management
By proactively managing risks, Cloudera protects its products and customers by anticipating potential threats, protecting assets, and reducing the likelihood of negative outcomes.
Vulnerability management
Our vulnerability management program enables our engineers to identify, evaluate, and remediate potential security weaknesses in order to protect our software and systems.
Security architecture and engineering
We help our teams make good decisions through secure development processes. Our security teams:
Develop/maintain security tool stack for all environments
Perform security architecture reviews
Conduct AI security reviews
Provide guidance and development support
Vulnerability management
Our Secure Software Development Life Cycle (SSDLC) framework ensures security is integrated at every stage, enabling targeted scans and analyses tailored to different aspects of the software. Before production deployment, all our products undergo thorough security-focused analysis and testing.
Software Composition Analysis
Software Composition Analysis (SCA) is an automated process for determining all components used to build a particular software component. This composition includes a listing of security vulnerabilities announced by the NIST National Vulnerability Database (NVD).
Cloudera uses SCA automation to find all dependencies with known vulnerabilities.
Static Application Security Testing
Static application security testing (SAST) improves software security posture by reviewing the source code to identify security vulnerabilities, bad practices, missing test cases, or hardcoded secrets.
All Cloudera software components undergo SAST analysis to ensure security defects are discovered before release. These findings are then built into the release planning process as early as possible to ensure that engineering teams have enough time to remediate before the release.
Dynamic Application Security Testing
Dynamic Application Security Testing (DAST) is a process that analyzes a web application for security vulnerabilities in the running environment. The automation simulates the activity that a normal user would perform, as well as malicious activity a hacker would perform. This aids in the discovery of vulnerabilities that are present in business logic or spread across multiple components that only present a risk after deployment.
Cloudera scans every release with automated DAST tools before production release.
Risk analysis
Cloudera performs scans on every release of our products. For any of the previously identified vulnerabilities, a risk analysis is performed to determine the following factors:
1. Inherent Risk
2. Mitigating Factors
3. Exploitability
4. Residual Risk
Cloudera uses the NVD CVSS scores and performs our analysis to determine if any given CVE or vulnerability may be exploitable in our software. Once the residual risk is determined, the work is given to Engineering.
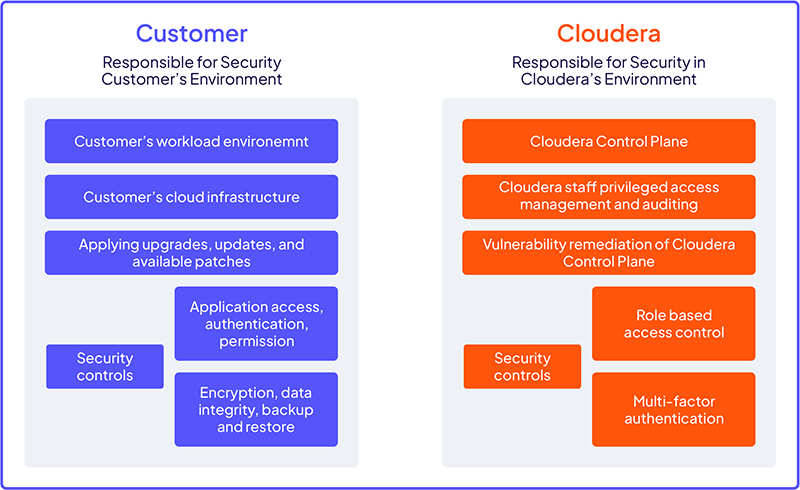
Customer data security
Cloudera provides the foundation for our customers to build secure and compliant hybrid environments. Our teams continuously engage with our customers to provide the best security architecture for their specific needs, from multi-cloud to on-premises.
Cloudera follows a shared responsibility model, providing customers complete control over the Cloudera compute and storage resources running in their workload account. With best-practice security features such as TLS everywhere, customers can deploy Cloudera in the most restrictive environments, allowing you to trust your most demanding workloads with Cloudera.
Comprehensive security awareness training program

Cloudera is committed to security and awareness training, including:
Dynamic and interactive content for every employee
Role-based security training
Security Awareness Month activities and celebration
Gamification and prizes
Modern phishing campaigns/targeted retraining and retesting

